For many product people, especially those coming from non-technical backgrounds, the Internet of Things can feel like a black box—full of acronyms like TPM, X.509, and LoRaWAN acronyms that intimate a lot of people. I recall the time a few years back helping a fledging startup brainstorm ways to use IoT to reduce fraud in pharmaceutical manufacturing. It’s easy to feel like you’re behind. But here’s the truth: IoT isn’t a mystery—it’s simply the natural evolution of how products connect, respond, and create value with the latest technology in the real world. In this article, I’ll break down what IoT really is, how it's productized in the market, and what’s happening under the hood—especially when it comes to security, where the greatest risks and most investable opportunities lie.
Image by macrovector on Freepik
What IoT Actually Is—Without the Jargon
At its core, the Internet of Things (IoT) is about connecting the physical world to the digital one—through smart devices, networks, data, and automated actions. Think of the latest thermostat that learns your preferences, a traffic light that adapts to congestion, or a heart monitor that alerts clinicians in real time. (yes, these are all real things, Google it). All these systems use embedded sensors to gather data, transmit it via secure networks, and trigger decisions or insights—automatically with or without human input. While often discussed in technical terms, IoT spans accessible, real-world applications across verticals like smart homes, industrial manufacturing, connected vehicles, and healthcare delivery systems.
How the Market Productizes IoT
While articles commonly refer to “IoT” as a single category, markets don’t buy IoT—they buy practical solutions to specific problems. In the home, consumers adopt products like Nest, Ring, or Alexa for comfort, safety, and convenience. In industrial settings, companies leverage predictive maintenance and automation platforms from Siemens or Rockwell to improve uptime and efficiency. Healthcare providers use connected devices from Philips or GE for continuous patient monitoring. In transportation, Tesla and OnStar exemplify IoT-driven innovations in over-the-air updates and fleet intelligence. Behind the scenes, platforms like AWS IoT Core and Azure IoT Hub provide the infrastructure to manage connectivity, authentication, and data flows. While the underlying systems are complex, most successful IoT offerings are verticalized bundles that abstract that complexity into seamless, integrated experiences.
How It All Works—Broaching the Technical
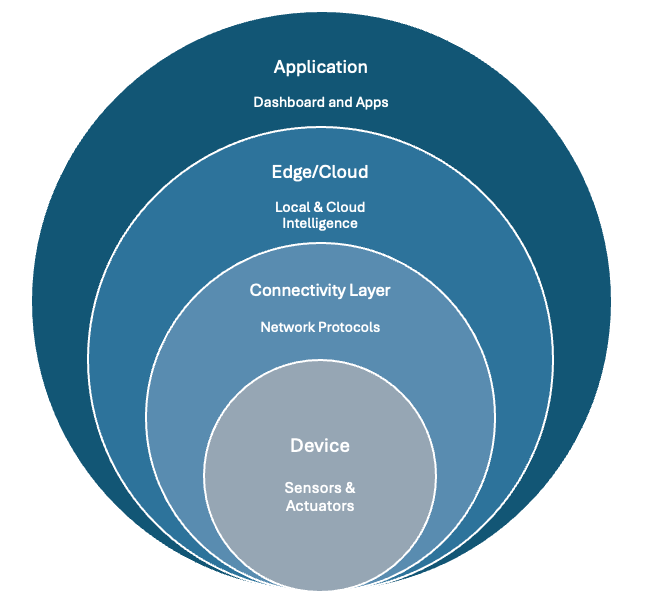
At a high level, IoT systems are built in layers. The device layer includes sensors and actuators embedded with firmware to capture or act on physical data. The connectivity layer relies on protocols like Wi-Fi, Bluetooth, LoRa, or 5G to transmit data. At the edge/cloud processing layer, data is filtered, processed, and analyzed—either locally at the edge for speed or in the cloud for scale. Finally, the application layer delivers insights to users through dashboards or mobile apps.
Devices typically connect to platforms like AWS IoT Core (https://aws.amazon.com/iot-core/) using secure protocols such as MQTT (https://aws.amazon.com/what-is/mqtt/) over TLS. Many are headless—designed to operate without a screen—and function autonomously once deployed. Data is continuously streamed, stored, visualized, and, in many cases, used to trigger automated actions. Leading solutions also support remote device management and over-the-air (OTA) updates, enabling fleets of devices to remain secure, compliant, and up-to-date without physical intervention.
To help demystify the technical layers of IoT to everyday devices, I provide this table.
Security Is the Hidden Giant
Behind the promise of IoT lies a massive—and often underestimated—challenge: security. With billions of devices deployed across homes, hospitals, factories, and vehicles, each endpoint represents a potential vulnerability. This is usually where Product people come in to demystify what’s going on here, confirm the right protocols are in place and develop programs to monitor it long term as we’ve seen real-world consequences, from hacked baby monitors to ransomware targeting industrial controllers and even cloned vehicle key fobs compromising automotive security.
At the heart of IoT security is device authentication—the foundation of trust. Devices use X.509 certificates (https://www.sectigo.com/resource-library/what-is-x509-certificate) , essentially digital birth certificates, to prove their identity to cloud platforms. These certificates are often backed by a Trusted Platform Module (TPM), a secure hardware vault that stores cryptographic secrets like private keys. Even if the operating system is compromised, the TPM keeps those keys out of reach.
Leading platforms enforce mutual TLS, ensuring that both the device and the cloud verify each other’s identities. Additional safeguards like secure boot and over-the-air (OTA) updates ensure devices remain uncompromised and up-to-date. Increasingly, organizations are adopting zero trust architecture, treating every device as untrusted until proven otherwise.
For investors and product leaders, the message is clear: the most resilient and scalable IoT platforms are those that prioritize security from the start. It’s not just a risk mitigator—it’s a competitive differentiator.
Product Can Play a Role
The IoT landscape isn’t reserved for hardware engineers and cloud architects. Its success depends just as much on product thinkers, strategic operators, and those who deeply understand customer pain points. There’s space—and need—for storytellers who craft compelling value propositions, analysts who extract insights, and business leaders who can model risk and scale. If you bring curiosity, clarity, and cross-functional experience, you already have what it takes. Don’t wait to feel ready—just start asking better questions.
TLDR
IoT is no longer an emerging trend—it’s a rapidly scaling reality. While the technology stack can seem complex, much of that complexity is manageable, especially when you start with a solid grasp of security. Imposter syndrome fades with exposure. If you understand risk, value, and user behavior, you already speak IoT.
Inspiration and Attribution
Image by macrovector on Freepik
What is the IoT? IBM, May 12, 2023
internet of things (IoT), By Kinza Yasar and Alexander S. Gillis, TechTarget, June 2024
Cybersecurity Asset Management (CSAM): Definition, Benefits, & Trends, Tanium, March 6, 2025